SonnieP
Member
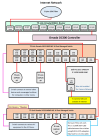
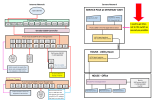
I am looking to take as much advantage of 2.5Gb connections as I possibly can. I need to make sure I am thinking correctly about how to best wire the network and make sure I am getting the proper TP-Link router and switch. I want to be able to control them via the Omada OC300 Controller that is already in the network. I have included the current and potential network diagram below.
Comments and recommendations are most welcome. Thank you!
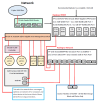
Comments and recommendations are most welcome. Thank you!